Eight Steps to Effective Ransomware Prevention

Ransomware attacks pose a serious threat to organizations in every industry. However, the risk isn’t limited to corporations. The data stolen is most often extremely sensitive consumer information as in these examples.
- BlackCat attacked NCR’s Aloha POS platform, disabling data centers managing transactions for thousands of fast-service restaurants. These select NCR clients were unable to process online meal and gift card orders and payments, as well as access some back-office tools needed for payroll processing.
- In February 2024, BlackCat remotely accessed a Change Healthcare portal that wasn’t protected with multifactor authentication. The hackers stole and ransomed protected healthcare information and personally identifiable information (PII) data that disrupted prescription, claim and payment systems for weeks. Change Healthcare paid the $22 million ransom. In April, a second group called RansomHub claimed BlackCat stole the ransom from them and said they were holding four terabytes of Change Healthcare’s data. The investigation is still underway, but the breach is expected to affect one-third of Americans.
- Prospect Medical Holdings, which operates 16 hospitals and 166 outpatient centers and clinics in California, Connecticut, Pennsylvania, Texas and Rhode Island, is facing multiple lawsuits after cyberterrorists Rhysida stole and posted screenshots of the company’s medical data. Rhysida claimed access to 500,000 employee and patient social security numbers, other personally identifying data, and medical record details that they threatened to sell if Prospect didn’t pay an estimated $1.3 million ransom. Former and active patients filed a class-action lawsuit against Prospect. Yale New Haven also filed a legal request to terminate a $435 million purchase agreement for three of the company’s hospitals, due in part to cybersecurity concerns.
- Royal, a cybercrime group, attacked the City of Dallas’ IT services, including sending ransom notes to the organization’s printers. The city’s police department website, 9-1-1 emergency responses, municipal courts, water utilities, and animal services were among the organizations disrupted during the attack. The hackers gained access to more than 30,000 citizen and employee records. Several months later, the Dallas City Council voted to reserve nearly $8.6 million for hardware, software, incident response and consulting related to the ransomware attack.1
Cyberattacks continue to plague businesses and implementing measures to prevent ransom-ware is a top concern for the C-suite according to 62% of CFOs – an 18% increase from 2022. These leaders struggle with inadequate staffing, complicated technology, generative AI sophistication and increasing attack levels.2
Unfortunately, hackers are relentless and gaining ground, particularly in the U.S. where the highest percentage of attacks (49.8%) occurred last year.3 The FBI received 2,825 ransomware complaints – 1,193 targeted at critical infrastructure organizations with losses totaling $59.6 million.4
In 2023, corporations paid more than $1 billion in ransom to fraudsters.5
These aren’t trends any organization wants to continue, except criminal enterprises, of course. Companies must understand how to identify risks and develop a plan for ransomware prevention.
What is ransomware?
Ransomware is a form of malware that fraudsters use to gain access and control of a company's network. They then lock the network, deny access to business-critical data and demand a ransom. Often backup systems are also disabled to prevent network restoration.
Ransoms are usually paid in cryptocurrency because it’s hard to track. But even if the company pays or otherwise regains access to its data, there’s no guarantee that the criminals haven’t already sold it to others. Or that they won’t target the company again. In fact, hackers attacked 78% of companies that paid a ransom again, requesting a higher ransom from 63% of these organizations.6
Remember, these are criminals without a high moral compass. If you think your company is too obscure to target, think again. Ransomware attacks aren’t just targeted at critical infrastructure or blue-chip corporations, and their initial goal isn’t to collect money. While ransomware schemes are designed to hold corporate networks hostage, they begin the attack with data theft.
Rather than pondering the likelihood of an attack, ask yourself these important questions:
- What’s at stake?
- How long can my company operate without the most recent data?
- What will be the long-term impact of a ransomware attack or our response?
Carefully consider not only the fiscal impact of an incident, but also the potential effects on your reputation, your customers, partners, and suppliers.
Which industries are most often attacked?
In 2023, healthcare (including public health) was the most targeted industry of all sectors attacked (see Figure 1). Critical manufacturing, which includes transportation, energy, water and utility systems and the government sector followed. Manufacturers, along with technology companies are targeted for proprietary intellectual property such as patents and processes. Financial services companies are obvious targets for consumer and business transactional data.
Figure 1
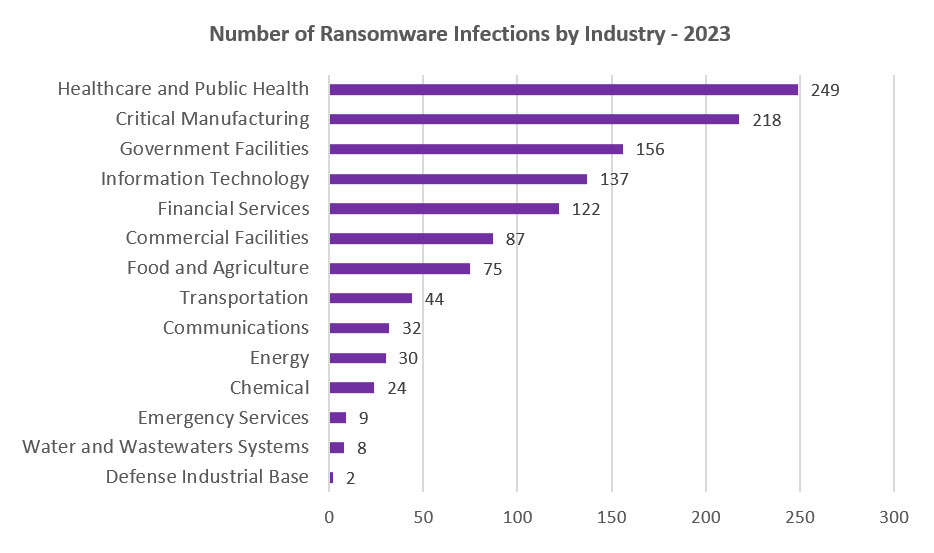
Source: Federal Bureau of Investigation, “Internet Crime Report,” 2023
Any organizations that collect PII, such as social security numbers, logins, and other sensitive data are frequently attacked to steal the data, which they can ransom and/or sell. For these organizations ransomware protection is imperative.
Be proactive to prevent ransomware.
Safeguarding the network, systems and data from any type of fraud should be every company’s overarching goal. So, it’s important to configure systems to achieve a strong security posture that reduces overall risks as well as prevents ransomware attacks.
-
Limit publicly shared and accessed information.
Fraudsters carefully study organizations before launching attacks. Social media and other online resources are treasure troves for spear phishing, which targets specific individuals and companies for details like job titles, interests, etc. Your social media policy should limit work-related information shared and online policies should limit the types of sites employees can access. -
Implement a multi-layered security solution.
Threats are constantly evolving. Your system and network protection should as well. The more layers, the harder it will be for fraudsters to penetrate your network. Focus on monitoring and prevention. It starts with an effective password manager and security system that denies fraudsters access. Multi-factor authentication further strengthens efforts to prevent unauthorized access.
Intrusion detection systems (IDS) scans network traffic logs for potentially malicious activities and issues alerts if any are found. Intrusion prevention systems (IPS) continuously monitor the network, blocking and reporting any malicious actions.
Antiviral and anti-malware software detect and remove malicious files, protecting against ransomware. Secure every device that touches your network. Out-of-date or jailbroken devices create open doorways for hackers. Also, secure and monitor remote desktop protocol (RDP).
If you haven’t performed a security audit in a while, now’s the time. You need to know where vulnerabilities lie and how to address them. -
Update systems regularly.
Your network design, implementation and maintenance can be a lifeline. Up-to-date hardware and software are simply harder to hack. Be sure you’re working with a nimble IT team that’s aware of the latest threats and countermeasures.
Insist on frequent network audits and scans for new accounts, open ports, and unusual remote connections. For example, some ransomware uses RDP and server message block to launch attacks – for ports 3389 and 445, respectively. Determine whether these ports should be accessible to only trusted hosts. Review both onsite and cloud settings.
Always apply security patches as they are released, automating this task if possible. -
Systematically back up data.
Consistently backing up data ensures a recent copy is readily available. Ransomware can encrypt backup drives. So, if you’re using a device, disconnect the drive after backing up data. Consider offsite storage and the cloud to further isolate your information. You’ll be able to return to a previous version that hackers haven’t encrypted. However, always test files before and after backup to ensure you haven’t saved infected files and protect against ransomware. -
Create an incident response and disaster recovery plan.
As equally important as ransomware prevention is a plan for how to manage it should an incident occur. Your employees will need to know exactly what to do if your data is compromised or your network is disabled.
An incident response plan establishes company-wide policies, roles and responsibilities to guide teams during a security event. As well as instructions, it should also provide a list of contacts and details for how and when to inform employees, customers and vendors.
A disaster recovery plan is a comprehensive guide detailing steps to recover as quickly as possible from unexpected events. These may include cyberattacks, natural disasters or any business disruptions. -
Restrict administrative rights.
Limit employees’ ability to install software as well as access to certain data. Only share sensitive information on a “need-to-know” basis. Group Policy Objects, a collection of client and system control settings, provide rules and restrictions for file executions. This further reduces the risk of installing malicious software and protects against ransomware. -
Train employees, remind and repeat.
Employees look for ways to efficiently accomplish often overwhelming workloads, which can lead to shortcuts or distractions. Fraudsters count on less attention to detail. Remind staff not to click on unfamiliar or suspicious links. Of course, everyone knows this. But given the sophistication of today’s cyberattacks, it can be hard to discern a legitimate email link from a phishing scam.
Employees may be confident enough in their IT network to think “a breach can’t happen here.” Train them to recognize and protect against ransomware themselves. Because cybersecurity may not be top of mind, frequent reminders and repetition are key. -
Report threats immediately.
Don’t hesitate to report an attack – even if you’re not certain there is one. The FBI encourages reporting suspicious or criminal activity to your local FBI field office or its 24/7 CyWatch team, available by email at CyWatch@fbi.gov or by phone at 855-292-3937.
If you see suspicious activity, it may already be too late. For example, BlackCat breached Change Healthcare’s portal nine days before demanding ransom. Develop an end-to-end plan to prevent ransomware before its needed.
Invest in cyber liability insurance for additional ransomware protection.
Cyber liability insurance covers a range of incidentals related to cyberattacks, including forensic investigations, regulatory fines, legal fees, business disruption and preventative measures. “Cyber extortion coverage” for investigation, ransom negotiation and payment can also be included in insurance packages.
Need help with ransomware prevention strategies?
Fraud is an ongoing problem but help is available. You can turn to local law enforcement, government agencies and professional associations for assistance.
- The FBI offers definitions and tips to recognize this and other types of fraud, as well as news. You can download a guide entitled “How to Protect Your Networks from Ransomware.”
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) offers many services, including free scanning and testing, malicious domain blocking and reporting, and an annual assessment. CISA has a comprehensive site that also features links to contact agency regional directors, as well as access to industry information, training, tips and news.7
- The U.S. Secret Service, through its Cyber Fraud Task Forces, helps law enforcement, companies and educational institutions investigate financial fraud. The agency also offers a “Guide to Ransomware,” other tools to prevent cyber incidents, and contact information for field offices.8
We can also help with ransomware prevention. If you’d like to learn more, complete a short form and a Synovus Treasury & Payment Solutions Consultant will contact you with more details. You can also stop by one of our local branches.
Fraud and Risk Management
Will Your Organization Make the Fraud 'Naughty or Nice' List?
Fraud and Risk Management
How Quick Service Restaurants Can Prevent Fraud and Protect Profits in 2025
Fraud and Risk Management
Guide to Cybersecurity Insurance: Why Your Organization Needs It
-
Will Your Organization Make the Fraud 'Naughty or Nice' List?
Protect your business from holiday fraud. Learn key stats, prevention tips, and how to recognize phishing, spoofing, and account takeover scams in 2024.
-
Interest Rates News: Fourth Quarter 2025
Get the latest Q4 2025 FOMC rate updates, forecasts and borrowing tips. Learn how interest rate changes impact loans, mortgages, and business growth.
Important disclosure information
This content is general in nature and does not constitute legal, tax, accounting, financial or investment advice. You are encouraged to consult with competent legal, tax, accounting, financial or investment professionals based on your specific circumstances. We do not make any warranties as to accuracy or completeness of this information, do not endorse any third-party companies, products, or services described here, and take no liability for your use of this information.
- Government Technology, “Dallas Cyber Attack More Extensive Than First Thought,” January 11, 2024 Back
- CFO, “85% of Cybersecurity Leaders Say Recent Attacks Powered by AI: Weekly Stat,” August 30, 2023 Back
- Cyberint, “Ransomware Recap: 2023 Report,” April 7, 2024 Back
- Federal Bureau of Investigation, “Internet Crime Report,” 2023 Back
- WIRED, “Ransomware Payments Hit a Record $1.1 Billion in 2023,” February 7, 2024 Back
- Infosecurity Magazine, “78% of Organizations Suffer Repeat Ransomware Attacks After Paying,” February 23, 2024 Back
- Cybersecurity and Infrastructure Security Agency, “Stop Ransomware” Back
- United States Secret Service, “Preparing for a Cyber Incident” Back
